Showing posts with label code. Show all posts
Showing posts with label code. Show all posts
Tuesday, February 7, 2012
Sweetness and HTTPS update
Both Sweetness and the HTTPS app have been updated today. Removed in page ads on both apps and a few bug fixes.
Saturday, March 12, 2011
My lame IR copy toy.
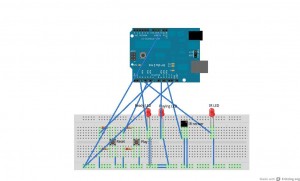
I got a sweet arduino for my bday and it kind of just sat around till i got a few things together to start work on my first project. Well i finally got off my ass, got all the shit i needed and got to work! I am about half way done and i thought i would share my progress so far. heres a little video of my toy in action and i go over the operation and components.
Here is a better view of how its put together:
And here is my uber 1337 code :P
Ok thats all i got, peace.
Here is a better view of how its put together:

And here is my uber 1337 code :P
#include < IRremote.h >
int IRRECV = 11;
int READYLED = 9;
int PLAYBUTTON = 5;
int IRLED = 3;
int RESETBUTTON = 7;
int PLAYLED = 2;
decode_results results;
IRrecv irrecv(IRRECV);
IRsend irsend;
void setup()
{
Serial.begin(9600);
irrecv.enableIRIn();
pinMode(READYLED, OUTPUT);
pinMode(PLAYBUTTON, INPUT);
pinMode(RESETBUTTON, INPUT);
pinMode(PLAYLED, OUTPUT);
}
int codeType = -1;
unsigned int rawCodes[RAWBUF];
int codeLen;
void rec(decode_results *results)
{
int count = results->rawlen;
codeLen = results->rawlen - 1;
for (int i = 1; i <= codeLen; i++) {
if (i % 2) {
rawCodes[i - 1] = results->rawbuf[i]*USECPERTICK - MARK_EXCESS;
Serial.print(" m");
}
else {
rawCodes[i - 1] = results->rawbuf[i]*USECPERTICK + MARK_EXCESS;
Serial.print(" s");
}
Serial.print(rawCodes[i - 1], DEC);
}
Serial.println("");
digitalWrite(READYLED, HIGH);
}
void play()
{
digitalWrite(PLAYLED, HIGH);
Serial.println(rawCodes[0]);
irsend.sendRaw(rawCodes, codeLen, 38);
delay(800);
digitalWrite(PLAYLED, LOW);
}
void reset()
{
int codeType = -1;
unsigned int rawCodes[RAWBUF];
int codeLen;
digitalWrite(READYLED, LOW);
setup();
}
void loop()
{
if (irrecv.decode(&results) && digitalRead(READYLED) == LOW) {
rec(&results);
irrecv.resume();
}
if (digitalRead(PLAYBUTTON) == LOW && digitalRead(READYLED) == HIGH)
{
play();
}
if (digitalRead(RESETBUTTON) == LOW)
{
reset();
}
}
Ok thats all i got, peace.
Sunday, January 30, 2011
BackupPC 3.2.0 XSS
I dont normally make posts about XSS exploits unless there is some special circumstances. I picked this one because BackupPC is a popular network backup tool that you might find in networks all over the place and because there is no built in security you normally only find it on "secure" trusted networks.
So anyway the issue is in Browse.pm. It gets a num variable passed to it via get request, then displays the unsanitary input back to the user. So heres PoCs of both the vectors i found.
PoC 1: http://target.server/cgi-bin/BackupPC_Admin?action=browse&host=realhostneeded&num=1[XSS] - comes back as a valid request and runs XSS
PoC 2: http://target.server/cgi-bin/BackupPC_Admin?action=browse&host=realhostneeded&num=[XSS] - comes back as ERROR and runs XSS
Like most XSS holes its a easy fix, just edit line 55 in /usr/local/BackupPC/lib/BackupPC/CGI/Browse.pm to read like so:
my $num = ${EscHTML($In{num})};
or download this Browse.pm file and replace it with the one in /usr/local/BackupPC/lib/BackupPC/CGI/ on the installed server.
Ok thats it, peace.
So anyway the issue is in Browse.pm. It gets a num variable passed to it via get request, then displays the unsanitary input back to the user. So heres PoCs of both the vectors i found.
PoC 1: http://target.server/cgi-bin/BackupPC_Admin?action=browse&host=realhostneeded&num=1[XSS] - comes back as a valid request and runs XSS
PoC 2: http://target.server/cgi-bin/BackupPC_Admin?action=browse&host=realhostneeded&num=[XSS] - comes back as ERROR and runs XSS
Like most XSS holes its a easy fix, just edit line 55 in /usr/local/BackupPC/lib/BackupPC/CGI/Browse.pm to read like so:
my $num = ${EscHTML($In{num})};
or download this Browse.pm file and replace it with the one in /usr/local/BackupPC/lib/BackupPC/CGI/ on the installed server.
Ok thats it, peace.
Thursday, November 18, 2010
HTTPS everywhere for chrome!!
Thats right girls, sX has another goodie up for grabs :D I really liked the idea EFF had with HTTPS Everywhere but was saddened when they said they will not be developing one for chrome due to some gayness, so i took the idea and ran with it. So today, with much pride, i bring you HTTPS "i know the name blows". HTTPS is a chrome extension that will look for HTTPS services on any host you goto, and given how you set it up it will just forward you to the https version of the site or display a icon you can click to goto the https version. Its still in beta so there may be a few bugs here and there but it should serve you well most of the time :) enjoy!
Current version: 0.7
DOWNLOAD: here
Current version: 0.7
DOWNLOAD: here
Saturday, September 11, 2010
JS via AS3
Heres a little script that runs javascript from flash.
swfjs.as
enjoy :D
swfjs.as
package {
import flash.display.*;
import flash.external.*;
public class swfjs extends Sprite {
function swfjs(){
ExternalInterface.call("function(){alert(1);}");
}
}
}
enjoy :D
Subscribe to:
Posts (Atom)